In a recent client meeting when we started discussing ‘Security Architecture’, I came across interesting views of what Security Architecture actually is. As a result of that discussion, I created a set of slides that describes how Security Architecture works. Of course, there are many ways to design Security Architecture but a common consensus of the how you view the topic is quite important to define.
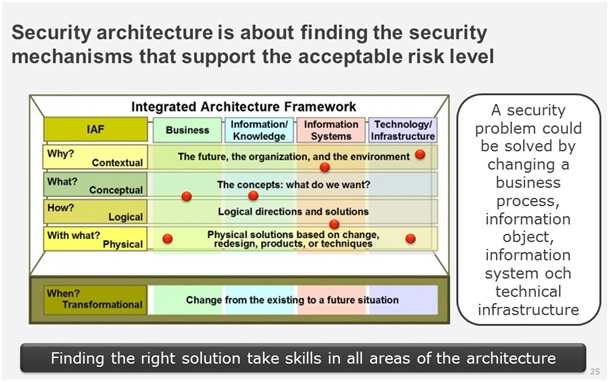
As you see in the above picture I use IAF (Integrated Architecture Framework) as a model to build my architecture. IAF is part of TOGAF since TOGAF 9. An architecture consists of four large parts: Business, Information, Information System and Technical Infrastructure. Security architecture is not a specific architecture within this framework. In some cases, you model an IAM-system and call it a security architecture but that is not correct. That´s a Technical Infrastructure architecture of a security system. A security architecture is actually something completely but it ends up in changing the current architecture you have to make sure that its secure. The red dots show examples where an architecture could be changed to make it secure.
So basically, ‘Security Architecture’ is the process of making an architecture more secure.

 English | EN
English | EN 

I want to be informed
Just and Necesary