CYBER SECURITY FRAMEWORK FOR HEALTHCARE
March 21, 2018
Abstract –As with any other sector, the healthcare industry is also prone to cyber threats. Though the nature of threats is similar to any other industries, it does need to address sector-specific risks along with security risks in its operating environments.
With Healthcare organizations increasingly finding the need to reassure their customers and regulators that their devices have incorporated adequate security measures, there is a growing demand to comply their organization’s security with various recognized security frameworks and standards.
Though numerous standards and frameworks available in the market, selection of the right framework to meet the organization’s need has become a challenge as organizations have to deal with various concerns related to these frameworks like standard inconsistencies, lack of prescriptiveness, compliance, cost, complexity, and certifications.
The Paper addresses some of the challenges faced by healthcare organizations in the selection of a security framework by reviewing some of the common standards and frameworks that are used by healthcare organizations around the world. The also paper highlights the advantages and disadvantages of each of the framework and offers guidance for organizations to select the right framework for compliance and certification needs.
Key Terms – ISO, HITRUST, Security Framework, NIST CSF, HIPAA, RMF
Security Framework for Healthcare
Healthcare organizations have always been challenged by the need for information security and privacy. Organizations are required to apply adequate safeguards to protect sensitive information and also to demonstrate compliance with respect to various state, federal and industry requirements.
Organizations have strongly desired for a framework that provides them methodology on implementing information security with the aim of achieving business benefits along with taking care of required legal and regulatory requirements.
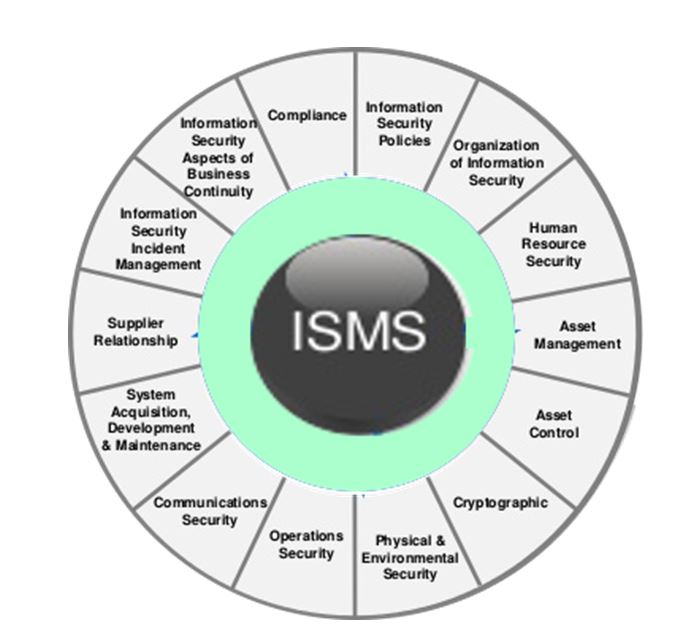
Over the years, many security frameworks have been leveraged by organizations from various industries to address the challenges of information protection. Healthcare organizations for long have relied on some of the standards used in other industries to address their security concerns and provide assurance to their customers.
With time, organizations have realized that some of these frameworks that are successful in other sectors do not fully address healthcare specific concerns. Due to the lack of prescriptiveness of some of these frameworks, organizations have not been able to adapt the principles, standards, guidelines and best practices from the framework to their specific context and develop practices that meet their own needs.
The following sections review some of the popular frameworks that have been used by healthcare organizations with aim of assisting organizations in the selection of framework that meets their organization’s needs of managing cybersecurity risks.
ISO 27001
ISO/IEC 27001 published by International Organization for Standardization (ISO) is a collection of Information security management best practices and provides requirements for Information Security Management Systems (ISMS). The standard was published in 2005 and revised in 2013.
The ISO 27001 is applicable to all organizations irrespective of their size and covers all sectors. It specifies the approach that organizations should use for information security and specifies the essential components. It also enables organizations to verify that risks are properly identified and managed.
To provide security controls to protect Personal health information, ISO offers the ISO 27799 standard targeted for the health sector. ISO 27001 can be integrated with ISO 27799 standards to address healthcare specific risks.
ISO 27001 is a risk-based framework and specifies 114 controls in 14 groups.
Pros: Compliance with ISO 27001 demonstrates to customers that the organization has put in place best practice information security process. By complying with ISO 27001, organizations can avoid the financial penalties and losses associated with data breaches, comply with business, legal, contractual and regulatory requirements, protect and enhance their credibility and reputations.
Cons: ISO/IEC 27001 is industry agnostic and does not completely address some of the healthcare-specific concerns. The requirements provided by ISO are also more generic and less prescriptive.
Compliance and Certification: Organizations can voluntarily choose to adopt ISO 27001 and can become ISO 27001 certified. This involves an initial audit and subsequent follow-up compliance audit to maintain the certification. The certification audit scope and requirement include a complete assessment of information security best practices applied to an organization.
HIPAA
Healthcare organizations driven by the need to comply with regulations have for long incorporated information protection in their systems. The Health Insurance Portability and Accountability Act (HIPAA) is one of the biggest drivers for organizations to protect electronic Protected Health Information (ePHI) against threats and hazards.
HIPAA defines the security rule that requires appropriate administrative, physical and technical safeguards to ensure the confidentiality, integrity, and security of electronic protected health information
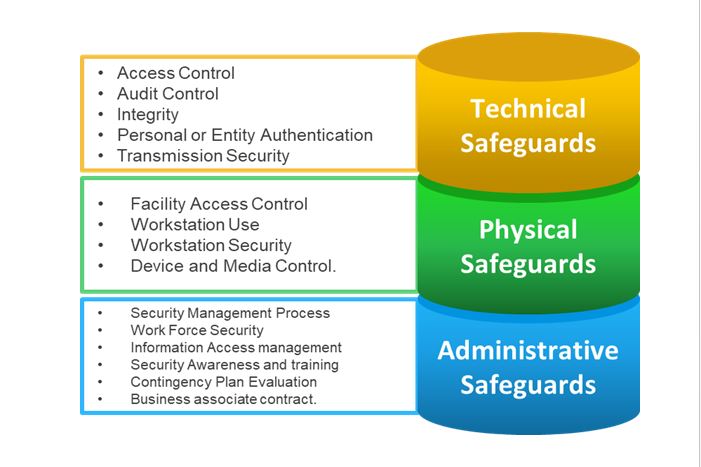
Due to HIPAA’s high-level nature of the requirements which are not being prescriptive, along with the absence of a complete risk analysis with just over-reliance on implementing various safeguards, the information protection programs across various organizations incorporating HIPAA have varied.
Without valid risk analysis and just complying with HIPAA security rule would result in an approach that does not handle all the threats that a healthcare organization is prone to.
Pros: HIPAA has been instrumental in the creation of a compliance culture in healthcare organizations. For most healthcare organizations HIPAA has become synonymous with security. Healthcare organizations have for long assumed their systems to be secure if it is compliant with HIPAA.
Cons: To prevent security violations, HIPAA defines security rule that consists of Standards and Implementations. The implementation controls are indicated as required or addressable which create a lot of ambiguity. Since HIPAA is not “certifiable” organizations are required to leverage external assessors or internal resource to perform self-assessment for compliance.
Compliance & Certification: Compliance with HIPAA requires organizations to either verbally commit to their customers or sign agreements to demonstrate compliance. In addition, organizations will also be required to provide compliance or attestation reports to prove compliance. Applicable organizations are required to use the SOC2 (System and Organization Control) reporting under AICPA(American Institute of Certified Public Accountants) control framework and other TSP’s (Trust Services Principles) for reporting HIPAA compliance.
The U.S. Department of Health and Human Services (HHS) has stated that there exists NO process for HIPAA certification. A statement from their website[1] categorically states the following “There is no standard or implementation specification that requires a covered entity to “certify” compliance. The evaluation standard § 164.308(a)(8) requires covered entities to perform a periodic technical and non-technical evaluation that establishes the extent to which an entity’s security policies and procedures meet the security requirements. The evaluation can be performed internally by the covered entity or by an external organization that provides evaluations or “certification” services. A covered entity may make the business decision to have an external organization perform these types of services. It is important to note that HHS does not endorse or otherwise recognize private organizations’ “certifications” regarding the Security Rule, and such certifications do not absolve covered entities of their legal obligations under the Security Rule. Moreover, the performance of a “certification” by an external organization does not preclude HHS from subsequently finding a security violation”.
HITRUST
HITRUST was formed by a consortium of healthcare organizations in 2007 with aim of making information protection a core pillar of healthcare information systems and exchange.
Developed by taking inputs from various healthcare and information security leaders, The HITRUST framework aims to meet the organization’s needs of providing specific guidance on the application of the framework to the healthcare sector.
As per HITRUST [1], the programs include the establishment of a common risk and compliance management framework (CSF); an assessment and assurance methodology; educational and career development; advocacy and awareness; and a federally recognized cyber Information Sharing and Analysis Organization (ISAO) and supporting initiatives.
The HITRUST CSF encompasses various federal and state regulations along with standards and frameworks such as HIPAA, ISO, COBIT, and NIST. The CSF offers a comprehensive, flexible and prescriptive framework for tailoring security control requirements for healthcare organizations of different scales.
The CSF uses the ISO/IEC 27001:2005 Information Security Management system as its foundation, primarily with the objective of supporting non-US business associates. The HITRUST CSF is structured similar to ISO 27001 and consists of six major components that include:
Control Categories: Includes various tropical information protection area like access control, privacy as defined in ISO 27001
Control Objectives: Includes various sub-topical information protection areas within a control category such as Mobile Computing and Teleworking, Openness and Transparency etc
Controls: This provides the specific information protection requirements based on ISO 27001 and includes a control reference number, name and specification that further describes the control.
Implementation Requirement Levels: For each controls three levels of a detailed and prescriptive requirement is provided along with associated risk factors.
Control Requirements: Detailed and prescriptive requirements contained in an information requirement level that support the control specification
Standard Mappings: The specific authoritative source that is directly or indirectly supported by the control requirements, such as NIST SP 800-53 r4 AC-19 or HIPAA 164.502(i)
There are 135 controls that cover security and some privacy-related requirements and 14 controls that cover specific privacy practices in the CSF
Pros: Leveraging the HITRUST CSF provides the following benefits
HIPAA Compliance: The prescriptive requirement provided by HITRUST CSF would help Medical device companies to respond to the implementation specifications and standards of HIPAA security rule
Federal Acceptance: Medical companies that implement the HITRUST CSF are more likely to get recognition from Federal agencies. These organizations are also more likely to receive federal assistance and grants. Implementing the CSF also eases the process of getting FDA 510(k) premarket approval
Limited Liability: Organizations that have implemented CSF are less liable in the event of a cyber-security incident. Companies also benefit by having to pay less premium for insurance provided if they follow robust security practices
HITRUST is a widely adopted framework across healthcare organization with nearly 80% percent of hospitals and health plans, as well as many other healthcare organizations and business associates, use the CSF. HITRUST is also recognized by AICPA and DHHS and is updated annually.
Cons: The HITRUST CST is not a standard in the same sense as ISO/IEC 27001:2013. Though it has been adopted internationally it is yet to be localized outside US English version.
Compliance & Certification: HITRUST is a certifiable framework that organizations can use for the creation, storage and exchange of personal health information. The certification process involves two-steps. Organizations first need to initially perform a self-assessment using a tool provided by HITRUST. Based on inputs provided to the tools, a customized assessment is created to assess the organization’s environment with respect to the compliance criteria. Corrective actions are suggested by the tools need to be incorporated. This is followed by a validated assessment is by third-party certified assessors.
Out of the 135 controls, 64 controls are required for HITRUST CSF Certification. Validated assessment results can be sent to HITRUST for certification. HITRUST will then create a report and will issue a letter of certification.
NIST CSF
To address the ever-increasing attacks on critical infrastructure, Nation Institute of Standards and Technology (NIST) has developed the Cyber Security Framework (CSF) that provides an incident management based model that various sectors or organizations can leverage for improving the management of cybersecurity risk.
The NIST CSF [4] framework is built on the foundations of threat modeling, threat intelligence, and collaboration. Leveraging such a framework helps organizations perform proper risk analysis, proactively address active and emerging threats and collaborate with various entities to effectively address cyber threats.
The Framework was created in response to the Executive Order (EO 13636) from President Obama in 2014 to strengthen the resilience of critical infrastructures and is widely used by all private and federal organizations in the United States.
Another Executive order in May 2017 by President Trump has made it mandatory for all federal agencies to adopt NIST CSF immediately.
The NIST CSF is structured into three parts consisting of:
Framework Core: This is divided into Functions (Identity, Protect, Detect, Respond and Recover) and then into 22 related categories(Asset Management, Risk Management etc), 98 sub-categories and for each sub-category references to other frameworks like ISO 27001, COBIT, NIST 800-53 are made.
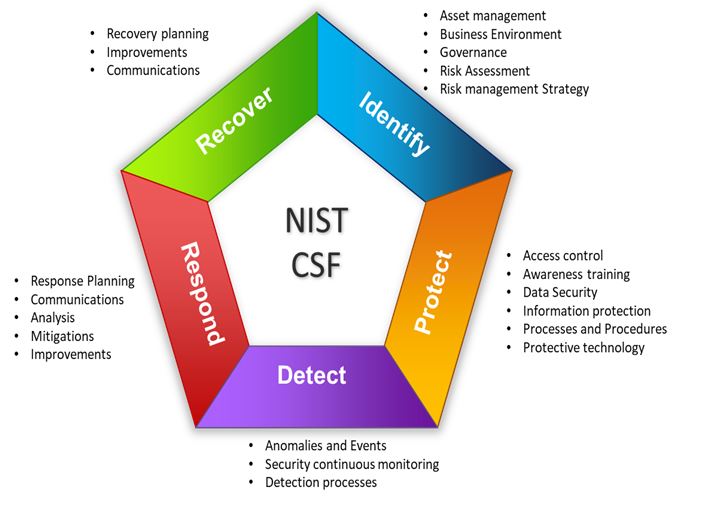
Framework Implementation Tiers: The tiers (Partial, Risk-Informed, Repeatable, and Adaptive). These define how extensively an organization manages its risks
Framework Profile: The profiles(current, target) helps organizations to assess its Current and Target Profiles.
The NIST security controls as defined in NIST 800-53 was specifically designed for US Federal agencies, but standards provided are also applicable for various non-federal organizations as well. NIST also offers a sector-specific document NIST SP 800-66
Pros: The framework is clearly structured in terms of the areas of security that need to be implemented. This enables both the top management, but also engineers and IT staff to assess the security and identify gaps.
Cons: The framework is new and is yet to gain acceptance outside the United States.
Compliance & Certification: The framework is not certifiable. However, an audit of the security controls that are aligned with NIST CSF can be performed as part of SOC 2 Type 2 Report audits.
OTHER FRAMEWORKS
Apart from the above-described frameworks, other frameworks have also been embraced by healthcare organizations. These include:
DoD 8500: healthcare organizations have used the Department of Defense(DoD) instruction DoDI 8500 Risk management Framework defined by the DIACAP ( DoD)
Information Assurance Certification and Accreditation Process for complying with defense requirements.
NIST RMF: The Risk Management Framework (RMF) draws a lot of parallels with the NIST CSF described earlier. The overall goals of both the frameworks are different. While the RMFs is targeted mainly for federal organizations, the CSF is meant only for private industries.
SUMMARY
To address the healthcare-specific needs various frameworks are available for organizations to choose from. The final selection of framework will be based on various parameters like scope, level of integration, industry specificity and applicability, prescriptiveness, scaling, tailoring, compliance, certification, shared assurance, assessment guidance, and tool support. The table below summarizes the various parameters organizations need to consider while selecting the framework.
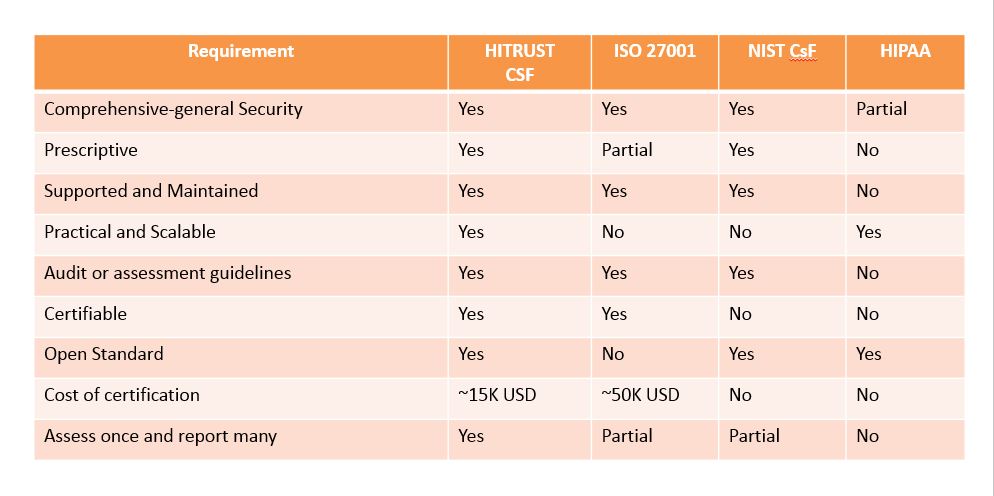
Conclusion
To gain credibility of their customers and to assure customers of information security, it is recommended for healthcare organizations to adopt a framework that supports certification.
Of the various frameworks that have been reviewed in the document, the ISO 27001 and HITRUST both offer certifications. For healthcare organizations selecting either of the frameworks will give good results, however, there is no clear winner in this content with each offering its share of pros and cons.
While ISO 27001 is globally recognized and is a better choice from a marketing perspective, it is not healthcare specific and is technologically neutral and industry agnostic. ISO is accepted in most countries as the de-facto framework for information security.
HITRUST combines the best practices from various other frameworks and is healthcare specific. It has the highest adoption rate with over 84 percent of hospitals and health plans, as well as many other healthcare organizations and business associates, making it the most widely adopted security framework in the industry.
References
[3] https://www.iso.org/isoiec-27001-information-security.html
[4] https://www.nist.gov/cyberframework
[5] https://hitrustalliance.net/documents/csf_rmf_related/CSFComparisonWhitpaper.pdf

 English | EN
English | EN 