Quality and Security are essential aspects of Code, we have several tools for application code static analysis, but what about Infrastructure as Code (IaC) like Terraform? This blog recommends a few such tools to help in Terraform code analysis.
Static Code Analysis on Terraform code gives a report on issues, its description, and ways to remediate the issue by checking your Terraform code with a set of security policies, best practices, etc. This results in improving the quality and security of your Cloud Infrastructure services. Below are industry-standard tools that help in scanning terraform code and can be integrated with your CI pipelines.
- Terraform Static Code Analysis using Checkov, TFSec
- Terraform Compliance testing
- Terraform security and compliance violations testing with Regula
Benefits of integrating these tools in CI,
- Improved security of Cloud services
- Security and compliance governance
- Apply standardized best practices
Let’s see them in detail –
Checkov
Checkov is my personal favourite tool for Static code analysis on terraform as it gives a comprehensive report on my Terraform Code and pinpoints how to resolve the issues. It detects security and compliance misconfigurations in your terraform code, it also supports CloudFormation, Kubernetes, Helm Charts, Dockerfile, etc. Checkov has a nice property of supporting scans of both HCL code and Terraform plan files.
How to integrate it into the pipeline?
There are multiple ways to integrate Checkov into the pipeline, below is one of the ways
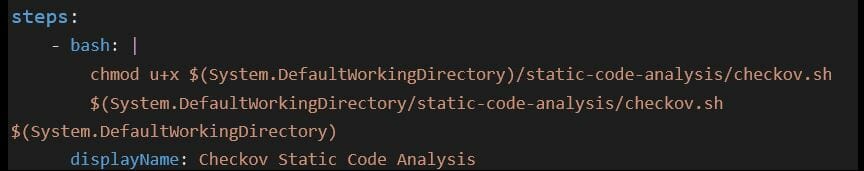
- Download checkov.sh and place it in your git repository
- Use it in your Azure pipeline as a step like below
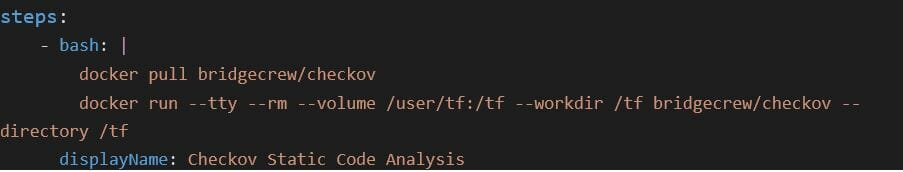
- Or you can directly use Docker in steps
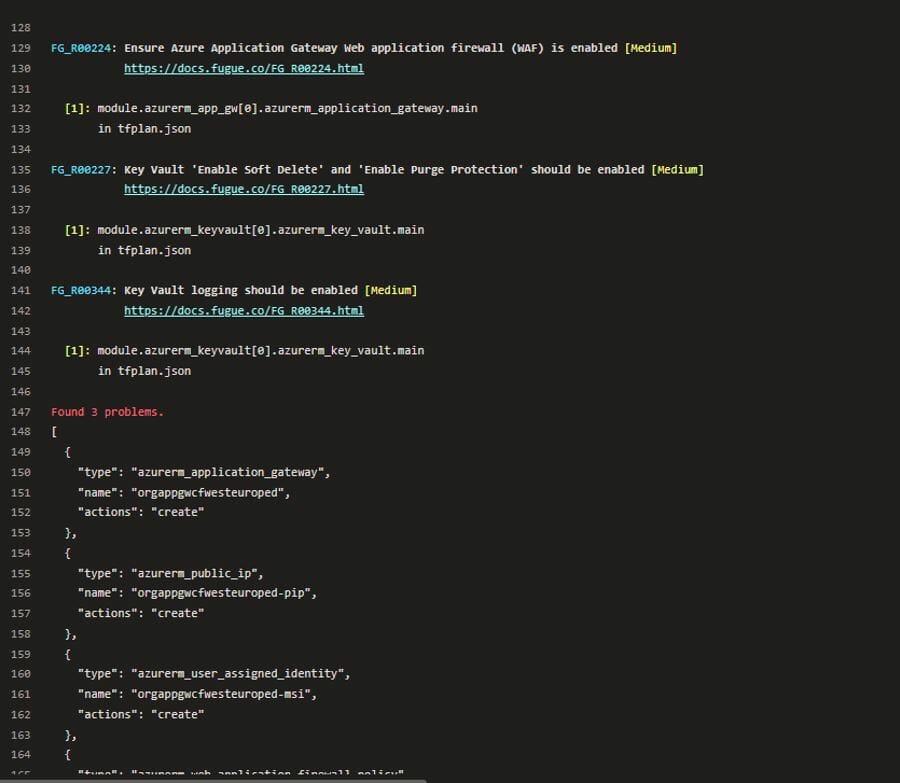
Example Output:
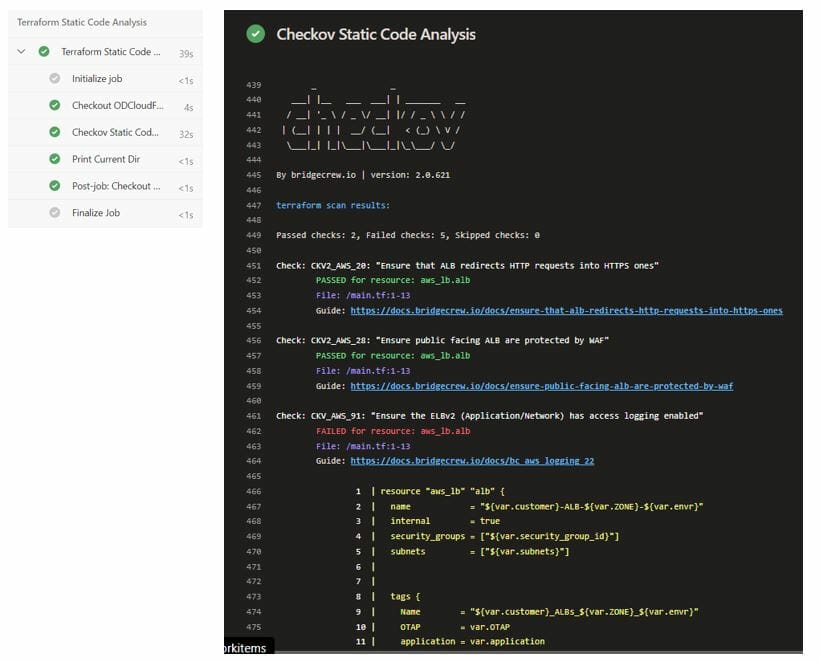
As you can see in the scan, it gives a proper Guide about the issue which is really useful in solving the issue.
You can also publish Checkov Terraform Quality Checks to Azure DevOps Pipelines.
TFSec
tfsec uses static analysis of your terraform code to spot potential misconfigurations. Its main superpower is it is very fast and capable of quickly scanning huge repositories. If you follow Thoughtworks Tech Radar, tfsec is recommended in Adopt which makes it more lucrative to terraform DevOps developers.
How to integrate into the pipeline?
The below example shows how to add tfsec in Azure CI Pipeline using Docker
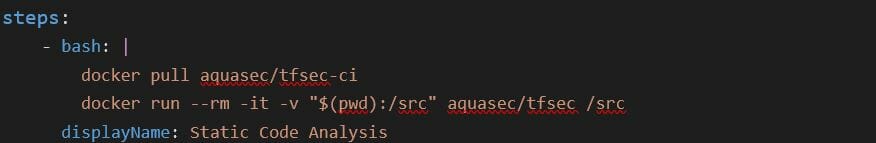
Example Output:
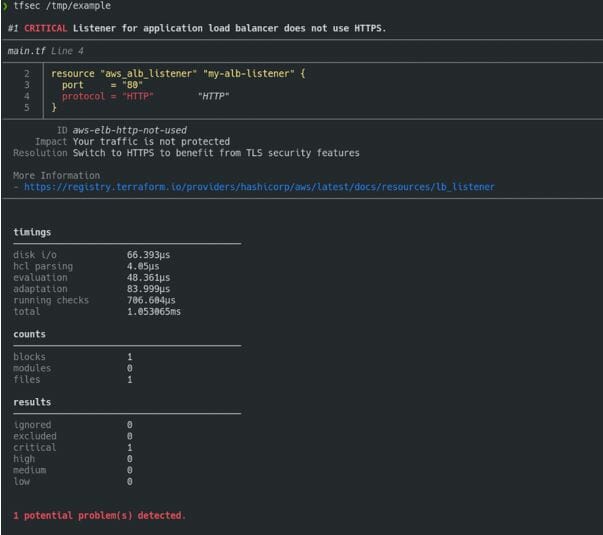
You can also publish TFSec Terraform Quality Checks to Azure DevOps Pipelines.
Terraform-compliance
terraform-compliance is a lightweight, security, and compliance-focused test framework against terraform to enable the negative testing capability for your infrastructure-as-code. It has a behavior-driven development language. terraform-compliance mainly focuses on negative testing instead of having fully-fledged functional tests that are mostly used for proving a component of code is performing properly. You can write feature files as in BDD for compliance as given below
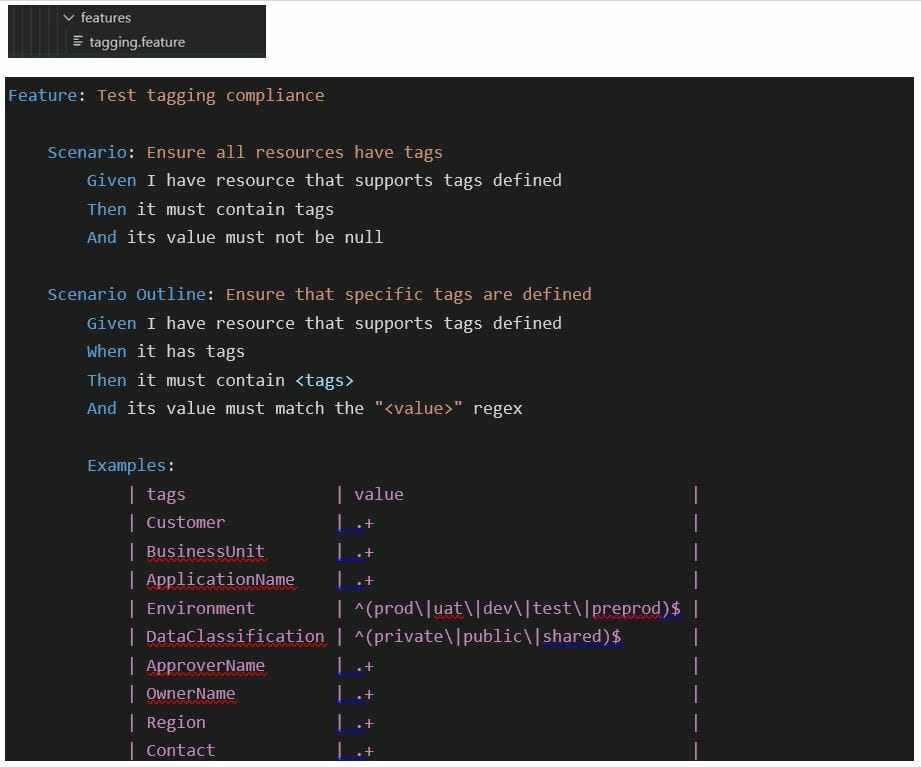
How to integrate into the pipeline?
The below example shows how to add terraform-compliance in Azure CI Pipeline using Docker
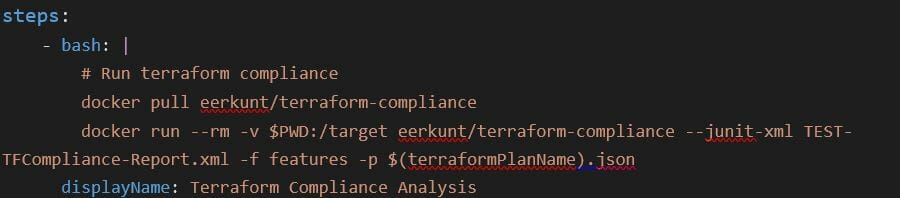
Example Output:
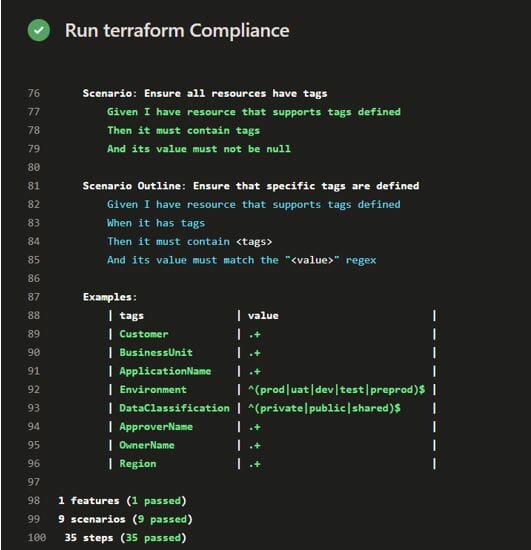
Regula
Regula is a tool that evaluates infrastructure as code files for potential AWS, Azure, Google Cloud, and Kubernetes security and compliance violations prior to deployment. Regula mapped Regula policies to the CIS AWS, Azure, Google Cloud, and Kubernetes Foundations Benchmarks so you can assess compliance posture. Regula might take longer to get started due to the need write our own rules, it is very expressive and it’s easy to write unit tests for it.
How to integrate it into the pipeline?
The below example shows how to add Regula in Azure CI Pipeline using Docker
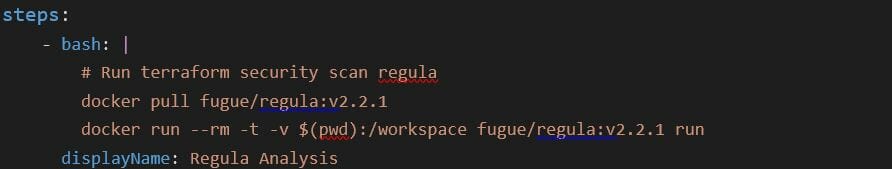
Example Output:
Integrating these tools in pipeline
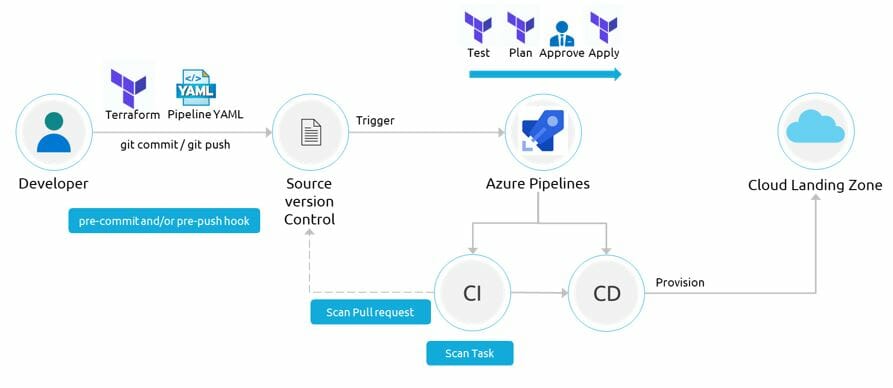
As shown in the diagram above, we can integrate the tools in,
- pre-commit and/or pre-push hook
- scanning pull request
- During CI build
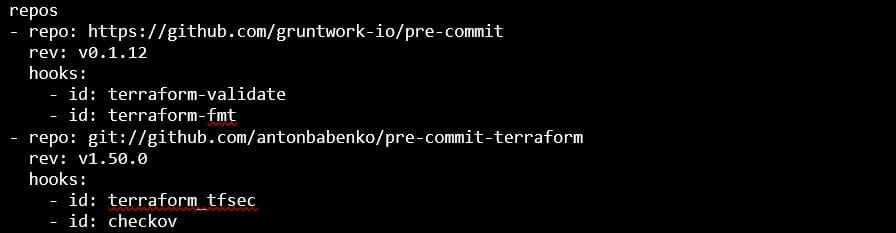
Example of pre-commit hook: .pre-commit-config.yaml
As shown in this blog, you can integrate these Terraform static analysis tools in your CI pipeline to achieve DevSecOps, where “Sec” refers to security and compliance.

 English | EN
English | EN 