The hackers are shifting left. Are your Enterprise DevOps teams ready for them? In a new eBook published by Sogeti and Microsoft, we discover why CSOs, IT directors and DevOps team leads must change their security scope to counter a growing threat. It’s the third in our series of guides to Modern App Development and Enterprise DevOps.
I’m delighted to announce the launch of Securing Enterprise DevOps Environments because the topic has never been more urgent. Many enterprises going through digital transformations are adopting DevOps as their new operating model for IT. And with Enterprise DevOps comes a new security conundrum — as you release software faster than ever, how do you ensure the security and compliance of your code, workflows, and infrastructure without negatively impacting the speed of delivery?
An expanding attack surface
Evidence shows us that the DevOps attack surface is proving an increasingly attractive target for hackers. In response, we must now broaden the security and compliance horizon. That’s because nefarious and creative hackers have started compromising developer boxes, infecting release pipelines with malicious scripts, and gaining access to production data via test environments. The threat is now present throughout the application development and maintenance lifecycle.
I can hear some people saying that hackers have been sieging production environments for decades, so what’s new? I agree and generally there are cyber security practices to prevent the hackers. However, the environment has widened significantly to include all supply chain tools and products that enterprises incorporate into their system. One breach at a third-party open-source tool can now lead to a global cyber security pandemic.
Three environments to protect
Clearly, it is no longer enough for enterprise security to focus solely on building and maintaining secure applications, yet this remains a common pitfall. Instead, the security scope must now extend to:
- The developer environment
- The DevOps platform environments
- The application environments
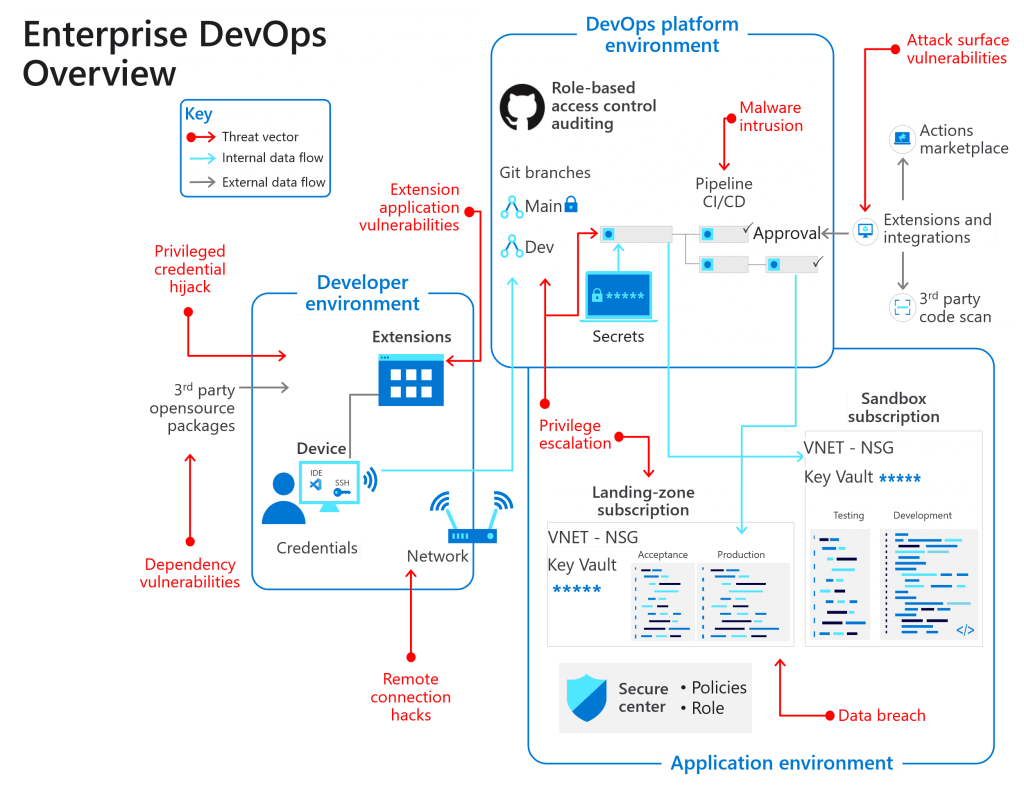
In our new eBook, we aim to help chief security officers (CSOs), IT directors and DevOps team leaders prepare their enterprise to deal with next-generation threats from shift-left hackers in all three environments. We define the best practices and platform capabilities you need to harden your enterprise’s security. We also provide examples of real-life hacks, examining how the breaches occurred and how each attack could have been stopped. For example, what would you have done faced with a $55M theft after a developer’s account had been hacked with a phishing mail?
From tools and culture to remote working
Our eBook explores the ideal secure and regulatory-ready setup of Enterprise DevOps tools and practices. These practices have shifted over the past two years with the work-from-anywhere business model. So, we also consider the impact of new remote working approaches that have seen an explosive growth in employees connecting from vulnerable Wi-Fi networks that present an open door to cyber attackers.
For the CSO, there is insight into securing the Enterprise DevOps environment without limiting business, as well as into recent ‘supply chain’ hacks and what’s needed to keep up with the fast-moving platforms. IT directors will find recommendations on modern security practices, team skills training and technical support, and platform teams. DevOps team leaders can find best practice guidelines around platform and tool capabilities, technical implementation and process change and implementation.
Read the eBook
Our objective throughout is to offer recommendations on how to fortify all three attack surfaces of Enterprise DevOps environments (developer environment, DevOps platform environments, application environments). Read Securing Enterprise DevOps Environments and discover the best practices and culture change necessary to thrive in our dangerous new world.

 English | EN
English | EN 