The addition I want to make is that:
- the ‘process’ realizes outcomes that are set by the goals and objectives of an ‘organization’, and
- the ‘process’ orchestrates business functions, which in turn use and produce ‘information’ streams.
I’ve visualized this in Figure 1:
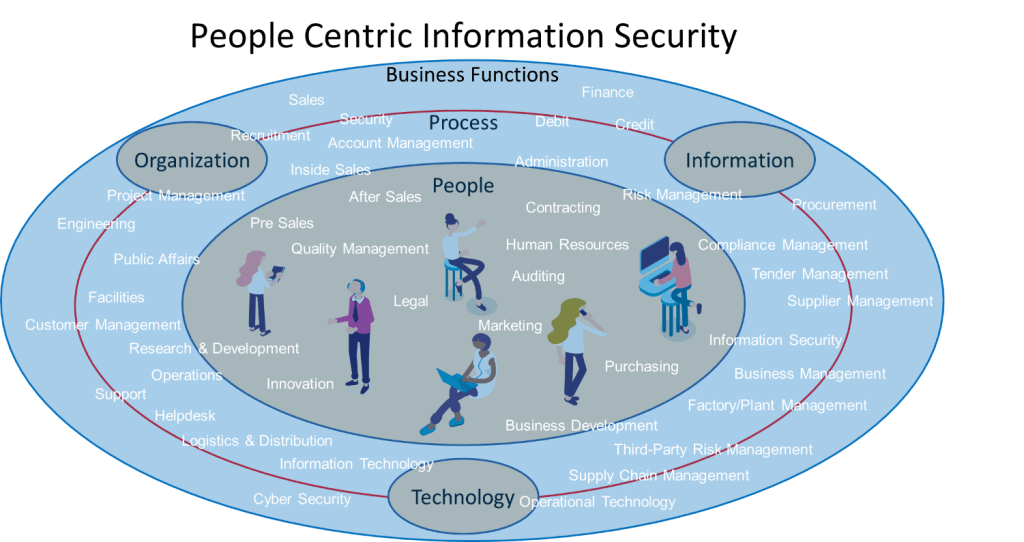
Figure 1: Visualization of People – Process – Technology, with the addition of (an impression of) Business Functions and Organization.
By taking business functions as a starting point, I am able to set people and information at the center of embedding Information Security. This approach helps explain how the ‘means’ (the technology that supports the organization) can best be designed to support the ‘end’ (meet user needs, with just the right security measures for balance between workability and security). Working like this will best safeguard the accomplishment of the organization’s goals and objectives, as it becomes part of the way people work.
Securing Information Streams: A New Approach
The next step is to find the best way to capture business functions and distill the information streams within them. The goal is that it is done in such a way that the information streams provide tangible context, allowing organizations to add ‘just right’ security measures. The information streams within business functions now become the primary object to secure. The measures are partly to be found in the construct of the technical environment, but mostly in the right understanding of the way people do their work, and how they (can) do this in a secure manner.
By focusing on information streams as the primary object to secure, it is easier to understand how to provide security. However, in my experience, organizations tend not to look at the inside of their organization to enhance security.
First Example
In Part I of my blog series, I illustrated that I see a lot of organizations using (new) law and legislation as a guideline to enhance their security posture. This means that they choose to adopt a certain security standard (e.g., ISO27K/NIST/CIS). Now, instead of implementing the guidelines within the chapters of that standard within their organization, they decide to start up a ‘Request for Proposal’ (RFP). They take the information from the security standard and ask for proposals from suppliers to deliver the security functionality to them. The supplier decides to answer the request and offers one or more technical solutions, with a project for implementation, management, and support to convince the requester to choose for their solution. Nothing wrong so far… except that the security standard is just that: a standard. And more than once the requestor fails to realize that there is no ‘one size fits all’ solution. They expect the winning supplier to implement the functionality within their organization, without any effort from their side. Fortunately, organizations are gradually starting to realize the ‘one size fits all’ approach doesn’t work, but these RFPs are still being published.
Second Example
Another example is that organizations, in order to get Information Security in place, focus on threats that come from the outside (e.g., malicious actors, hackers). They then try to understand how these malicious actors work, and then choose a technological solution (tool), often on the top-right side of some quadrant, to prevent malicious actors from compromising their environment. Don’t get me wrong, keeping these individuals out of your organization is an important goal for Information Security. The challenge is that, by not looking at the security requirements from the inside perspective, the functioning of the chosen tool can in fact decrease workability (and productivity). Also, people might look for ways to circumvent it. They start searching work arounds, possibly using Shadow-IT, making the investment worthless. The organization feels it has done a good job in becoming more save, the opposite is true. For both examples the same basic rule applies; it is impossible to enhance information security without taking the effort to understand the organizational context.
Introducing the People Centric Information Security Framework
Setting information streams as the starting point isn’t an easy task. It requires involvement and actions from people within the organization that often haven’t been involved yet. And it requires awareness and actual behavior around the fact that:
- the security department is responsible for the security process,
- everyone that processes the organizations information is responsible to follow and execute that process.
To help realize this, I created a framework to implement an Information Security Management System (ISMS). Don’t worry, I do not intent to replace existing security frameworks. They are still very relevant, and you are able to use any of them in conjunction with this framework.
I created this framework because I couldn’t find the ‘how’ in the existing frameworks. Most frameworks exactly explain ‘what’ Information Security is and which components are part of it. And it explains ‘why’, ‘when’, and ‘where’ these components are to be considered. This is of course very important, you don’t want to miss any of those components, as your security is as strong as its weakest link. In time however, I felt that I understood the ‘what’, but I couldn’t really find a framework explaining the ‘how’. This is why I started to work on this myself.
Business Benefits of the Framework
My framework describes the steps within the information security process. How to set responsibility, and how those responsible are able to take their responsibility and act on it. It also shows how Cyber Security is placed within Information Security, which helps to keep the two separated and prevents people from confusing them. It is a standard, context-based approach to implement an organization specific, tailor-made, Information Security process. An approach an organization wants to implement because it contributes to their:
- business
- customers (or citizens/companies for governmental institutions) and
- employees.
And it is an approach that will, in the end, lead to profit, because it will optimize your organization’s processes. Process optimization allows processes to perform in their most efficient and effective way. This in turn allows you to speed up your business. Not because you have digitized your information, but because you have created the context around it. That context offers you “brakes” to go slower, or make an emergency stop when obstacles arise.
As my framework starts with setting up information governance, as a prerequisite to realize Information security, and the execution of governance lies with people, I chose to call my framework the ‘People Centric Information Security Framework’. A step-by-step approach on how to realize Information Security into reality. Making people aware of this approach is the first step. And, as with all change, to answer and overcome the resistance and obstructions that will surely come my way.
Concluding
I realize that I have set the bar high, claiming to have created a framework that explains how to implement information security within a business. I do stand by my claim. It isn’t an easy task to implement information security (if it was there wouldn’t be so much ado around it), but, with the right mindset and a step-by-step approach, it is possible. In fact, I use it every day, and it really helps to get Information Security on track… Having said that, I still struggle with the fact that not everybody has the right mindset… at least, not yet! Hopefully this blog series will help change the mindset, at least a little bit. The quicker we realize this, the easier it will become to realize information security.
In my next blog I will further elaborate on how I perceive information streams and why they are so important to realize information security.

 English | EN
English | EN 