INTERNET OF THINGS: INTERCONNECTION MEANS NEW SECURITY AND TESTING CAPABILITIES
August 20, 2013
More and more devices are (or will be in the near future) connected to other devices or to Information systems (IS) which manage or monitor these devices. This trend calls for new approaches and reinforcement of security and testing procedures in order to protect both side: the device itself with people who use it and the IS which monitor/manage the device.
Quite recently (last month and last year), different examples show that investments must be made in this area.
The first example is coming from e-health sector ([1] and [2]):
- 1) In one episode of the show Homeland, the Vice President of the USA is assassinated by a group of terrorist that have hacked into the pacemaker controlling his heart. Of course, it is only fiction but …
- 2) A researcher hacked his insulin pump using an Arduino module that cost less than 20 USD and Barnaby Jack (who died few weeks ago), at this time a security researcher at McAfee, demonstrated a system that could scan and compromise insulin pumps that communicate wirelessly.
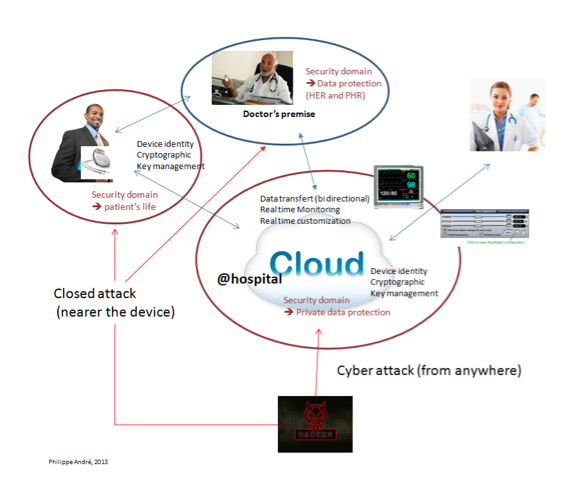
In this example, the well known and literature covered data privacy hacking is outdated: it is no longer about only protecting data of the people (privacy issue), it is about data security and life continuity of the people using the embedded (in their body) devices: it is ensuring that the behavior of the device will not be jeopardized.
Implanted devices have been around for decades, but only in the last few years have these devices become virtually accessible. While they allow for doctors to collect valuable data and monitor them, many of these devices were distributed without any type of security or defensive mechanisms in place. Even worse, a professor at the University of Massachusetts-Amherst [3], discovered that many medical devices use poorly developed code that could lead to deaths, injuries, or security lapses. Cross medical-Industry protocol for coding QA, security and testing are poorly developed or nonexistent. But, apart from standard software development process, new security features and approach must be implemented for these devices.
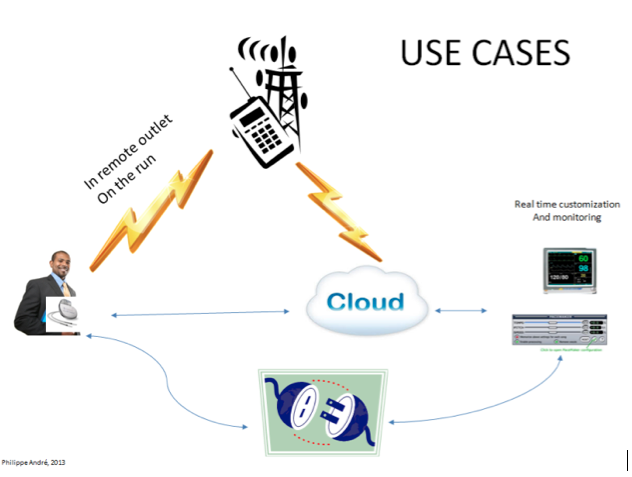
Today, this type of device is usually access directly via specific equipment used by doctors in hospital, or monitored via internet. But in the near future, and in order to develop e-Medecine in remote outlets, the mobile network (3G and 4G) will be used, simply because everybody has (or will shortly have) a mobile phone.
So, different security domains must be defined at service level (i.e. device and other software elements). As in a lot of areas, building security walls (Firewall, proxy, DMZ) for several software components (typically enterprise IS behind the firewall) is no longer valid for these embedded software. Security domain covers a consistent level of security depending of the use cases (i.e. behavior of the device): it is obvious that protecting person’s life does not require the same level of security that accessing people data in an e-Health system (one could be lethal, the other is not).
The other example comes from transport sector. Same kind of security requirements can be found about boats and cars navigation. In late July this year, the GPS system of a yacht was hacked and a wrong route was given to the crew without noticing it [4]. The scientists behind this experiment operated from the deck of the boat to intercept the GPS signal, but the team says it is also possible up to 3 kms from boat. We can imagine the same thing with cars in the near future (car hacking via Bluetooth or GPRS and SMS is already well known), which will be more and more connected to the internet and navigation systems, or with other surrounding cars or road equipment to reinforce driving security in real-time.
As the digital and physical worlds continue to coalesce, we are going to need aggressive systems of securing, testing and updating these new use cases. The devices of yesterday and their embedded software were not created to protect against the threats of tomorrow.
References:
[1] Yes, You Can Hack A Pacemaker (And Other Medical Devices Too), Forbes, 12/06/2012
[2] Medical Cybercrime: The Next Frontier, fast company, August 2012
[3] http://www2.technologyreview.com/TR35/Profile.aspx?TRID=760, and “Take two software updates and see me in the morning: The case for software security evaluations of medical devices”, Steven Hanna, Rolf Rolles, Andrés Molina-Markham, Pongsin Poosankam, Kevin Fu, Dawn Song (2011), 2nd USENIX Workshop on Health Security and Privacy. USENIX Association
[4] Un yacht piraté en détournant le signal GPS, Le monde informatique, 31/07/2013

 English | EN
English | EN