IDENTITY ACCESS MANAGEMENT ON CLOUD
June 10, 2019
As more and more customers are transforming their applications to cloud the main questions arises are:
- How do I secure my data and processes while it’s running on cloud?
- How do I make sure all my applications are secured with proper authentication and authorization approach implemented?
Answers to the above questions are something which are expected to be provided by the vendor supporting them into their cloud migration journey. If vendors are right on spot to provide the answers correct and assure the customer about the correctness of the approach then it could become one of the major factor in winning the business for certain customer domains.
In order to protect the customers’ assets & data on cloud, hundred percent correctness of Identify Access Management solution is a must. For any Identity Access Management solution on cloud given below are the concerns needs to be addressed:
- Bulk User Handling via Process using Files
- On premise Identity Provider i.e. AD as core provider
- Cloud Hosted Integration Identity Provider i.e. cloud IAM in B2B and/or B2C modes
- Sync with core Identity stores i.e. AD and cloud IAM
- RBAC based User access for Cloud platform services
- Role Based User Access to applications
- Monitor & Self-Healing
The implementation of all the above points in an Identity Access Management solution would typically have different blocks as shown in the below diagram:
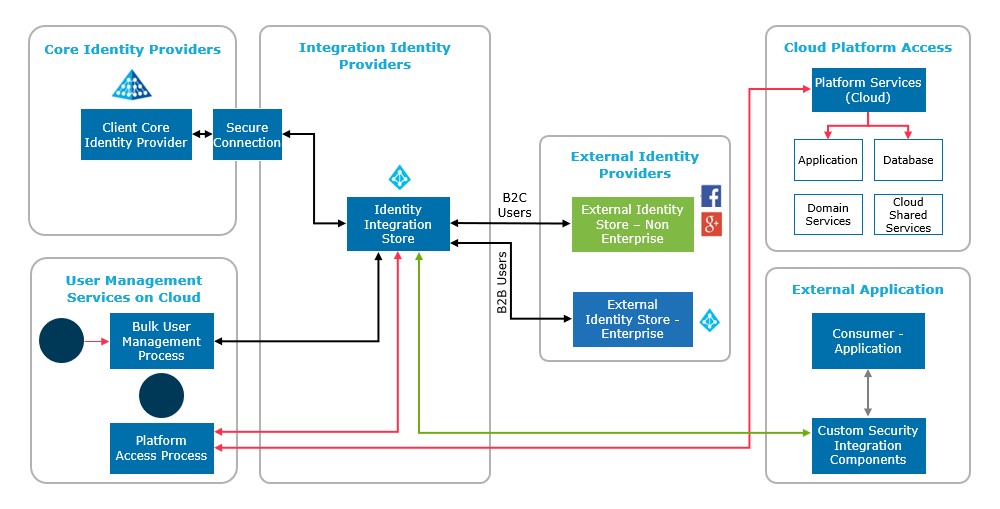
A brief description of each of the block in the diagram looks like as below:
Core Identity Providers – On-premise Enterprise Identity Providers like AD which any customer would have at on-premise in their existing portfolio.
Integration Identity Providers – Cloud Hosted Identity Management Solutions used as central integration store for domain, B2B and B2C users.
External Identity Providers – B2B and B2C user identity stores integrated with central Identity Provider store.
User Management Services – User handling processes to maintain the onboarding and decommissioning of users.
Platform Access – RBAC solution built for giving access on cloud platform to application and platform users.
External Application – Are applications leverages IAM solution to access applications using B2B & B2C RBAC approach for its end users & applications.
In this way, identity access management flow shown above helps to implement authentication and authorization solution for different scenarios like domain users, B2B & B2C applications & users.

 English | EN
English | EN 