Often you see people hacking in movies and series, and it is a load of bogus. Mesmerizing 3D glasses and special gloves? No one actually hacks like that. But what movies or series actually kind-of, approximate the real deal? In comes Mr. Robot!

This series (I watched in on Amazon Prime) is acclaimed for the accuracy and shows how hacking can be done with actual tools that hackers use.
I’m not a hacker. As a software engineer, I’ve always been interested in how people break into my stuff, especially using crafty ideas and social engineering. In this blog I’m highlighting some of the tricks the main character uses to hack and crack his way into many systems.
Basic starting knowledge
Let’s start out with some common knowledge that is needed to pull these things off. First of all (basic) programming and scripting knowledge should be present! Most tools needed are based on command-line interfaces and can be called using scripting. Also, knowing and understanding how different Operating Systems work is important. Sometimes you run on Windows, and sometimes on Linux. You should be able to find your way around in those systems regardless. Last but not least networking should be part of your bag of tricks. You really need to understand IP addresses, routing, subnets, ports and that kind of stuff. Accessing PCs or devices remotely requires understanding of these components.
Kali Linux
What really stood out is that the main characters default OS is Kali Linux. This is the most prominent penetration testing and ethical hacking Linux distribution out there today. It runs on many different devices and pretty much runs on every laptop you have lying around. I’ve installed Kali on some old Lenovo Yoga and it runs smoothly.
The reasons many hackers use Linux in the first place is that most tools are, basically, written specifically for that platform. Also, the open-source license is attractive, and the extensibility is enormous.
DeepSound
Technically speaking not hacking, but in the series, the main character often hides files. He uses a tool to embed files and pictures within audio files and burns them on a CD. This is called seganography and the tool used is DeepSound.

So, how does this actually work? You can simply download the tool and run it! You can then open ‘carrier’ files, in this case audio was used, and ’embed’ another file in there:
As you can see in the screenshot, you can basically embed your secret files in any audio file. Nowadays audio CDs are for old people like me, but still, hiding a CD in your collection is pretty nifty if you ask me!
Internet of Things
In several episodes, rogue Raspberry Pi’s were used to hack HVAC (climate control) or even UPS and power supplies. While that seems a bit far-fetched, one thing stands out. The main character uses an actual search engine for internet connected devices called Shodan. Sometimes called the search engine for hackers, and even ‘the world’s most dangerous search engine‘, the search engine can be invaluable for hackers. Shodan basically finds webcams, traffic systems, anything connected to the web on the common ftp/ssh/telnet/snmp/sip and of course web ports.
Running a simple search for IIS (Internet Information Services, a widely used Microsoft webserver) shows us the following results:
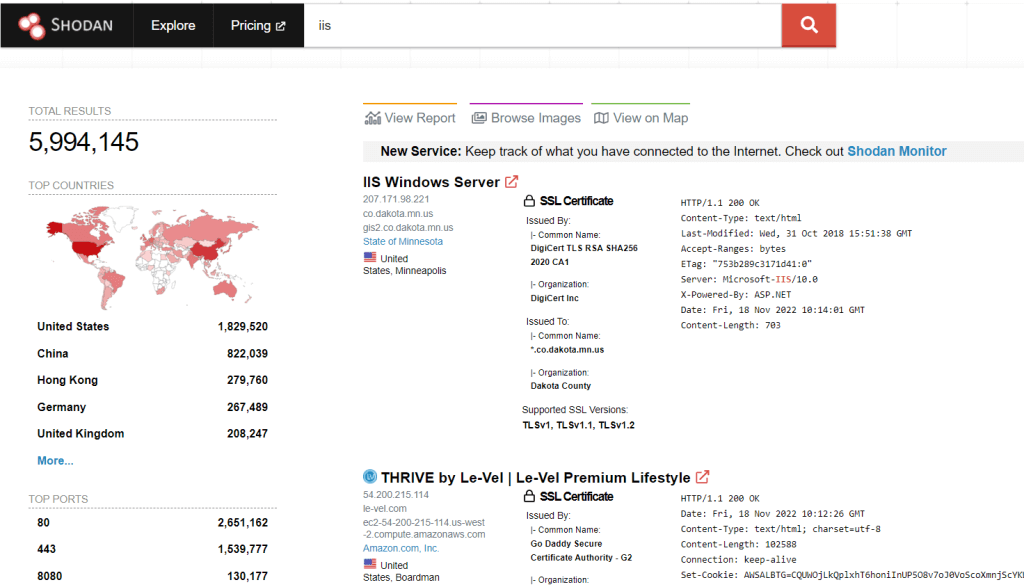
You can imagine that if a vulnerability arises for IIS, you can (mis)use this information to your advantage…
Start your journey
While I’m not an advocate of any of the readers to start hacking everything you see, it can be really useful to understand how these things work. Everything starts with awareness and understanding these tools can open your eyes on how to connect devices, or even how to write your code.
This blog stated some of the tools used in the show. You can freely start using Kali Linux and for example spin up a Raspberry Pi to see how the tools work.
Final remark; watch the show! Drop me a line if you’re a fan like me!

 English | EN
English | EN 