Have you ever wondered how “cyber” became the go-to prefix for anything technical? Terms like “cybersecurity” and “cyberattack” are everywhere, but the roots of this terminology might surprise you.
The term “cybersecurity” first appeared in 1989, rooted in “cybernetics”—a field introduced in 1948 by Norbert Wiener, which explored communication and control in machines and living beings. In the 1990s, “cyber-” became a popular prefix to evoke futuristic or technological ideas, leading to terms like “cyberlaw,” “cyberwar,” and, of course, “cybersecurity.”
Despite its widespread adoption, cybersecurity is only one aspect of the broader field of information security. The latter focuses on protecting all forms of information—digital, physical, or otherwise—by addressing how people, processes, and technology interact.
This shift in terminology has created confusion:
Cybersecurity highlights the technical layer but can overshadow the human and process elements of security.
Information security, by contrast, emphasizes a holistic approach: people handling information, the value of that information, and the impact of incidents on business continuity.
Why does this distinction matter?
Because not everyone needs to be deeply technical to contribute. Educators, analysts, and risk managers all play critical roles in keeping information secure, alongside the technical experts who build and defend systems.
Understanding the historical context of cybersecurity reminds us that resilience in security comes from diverse skills and perspectives, not just technical process. Let’s make space for every contribution.
Your thoughts?
As I discussed in this blog, the term ‘Cybersecurity’ often shifts the focus of ‘Information Security’ towards securing technology. This is understandable, as the word ‘cyber’ is closely associated with technology.
However, it’s important to remember that technology is a supporting element. It helps organizations and people process information more effectively and efficiently, but it’s not the sole focus of information security. Using the term ‘Cybersecurity’ without a broader understanding can lead to the pitfall of thinking a secure environment is achieved solely through technology—or worse, making technology the end goal rather than a means to an end.
I created this image to illustrate the key elements required for securely processing information: people, processes, organizations, and the information itself, with technology serving as a vital enabler.
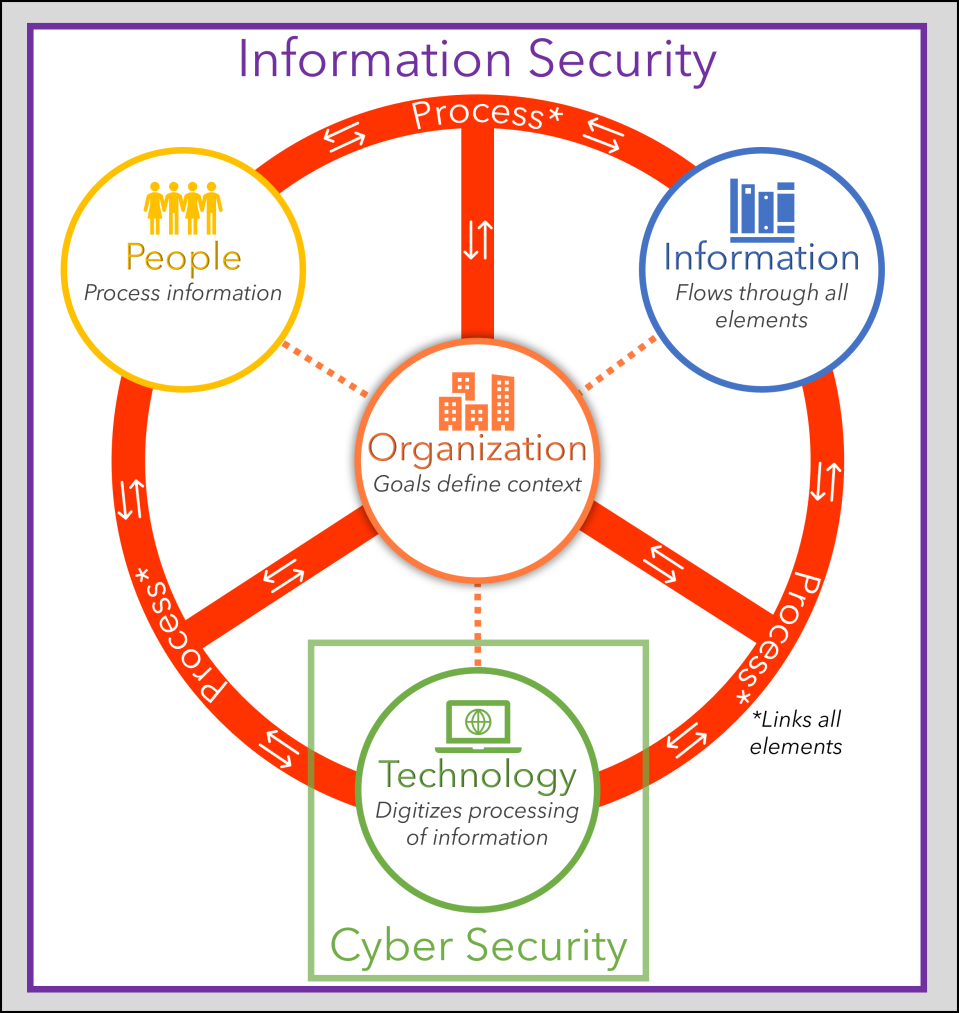
What are your thoughts on this perspective? Does this image resonate with how you approach security in your organization?

 English | EN
English | EN 