This blog provides a structured approach to designing an enterprise-scale landing zone in the cloud. It outlines key concepts, design patterns, security considerations, and best practices to ensure scalability, security, and operational efficiency in cloud adoption.
What is a Landing Zone and Its Importance
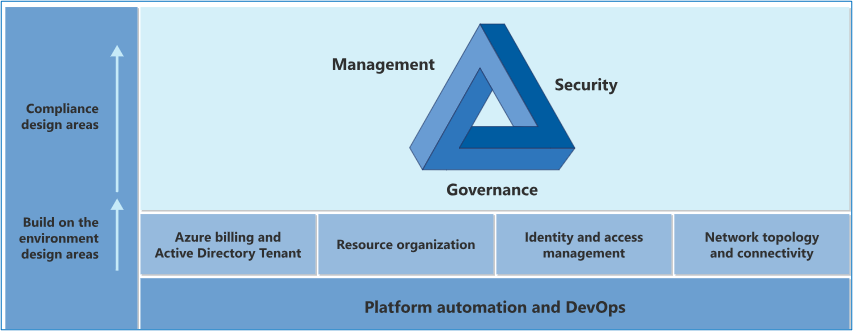
A landing zone is a pre-configured, scalable, and secure cloud environment for hosting applications. It is built following best practices and design principles to support enterprise-scale cloud adoption and serves as the foundation for cloud workloads and applications.
Importance in Enterprise Scale Landing zone:
- Scalability & Agility: Establishes a repeatable environment that grows with organizational needs.
- Security & Compliance: Incorporates standardized security controls and governance policies.
- Operational Efficiency: Centralizes shared services (e.g., identity management, connectivity, monitoring), reducing duplication and simplifying management.
- Cost Optimization: Enables cost control by streamlining resource allocation and implementing billing policies.
- Risk Reduction: Defines network topologies, identity controls, and security frameworks to minimize misconfigurations.
Types of Landing Zones
Landing zones are generally categorized into two types, each serving distinct purposes while working together
- Platform Landing Zone
- Application Landing Zone
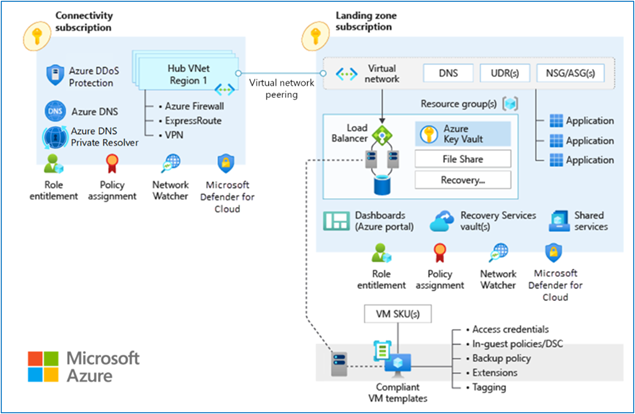
Platform Landing Zone
A dedicated subscription (or set of subscriptions) that hosts shared services such as identity, connectivity, management, and security tools.
Key Characteristics:
- Centralized Management: Enforced organization-wide policies by central IT teams.
- Shared Services: Networking, logging, security, and monitoring services available across applications.
- Governance & Compliance: Acts as the control plane for governance, ensuring all environments adhere to established standards.
- Operational Efficiency: Consolidates resources reducing operational overhead.
Application landing zone
A subscription dedicated to hosting specific applications or workloads, provisioned via automation and governed by management policies.
Key Characteristics:
- Decentralized Deployment: Managed by application teams while maintaining central oversight.
- Tailored Environment: Configured for performance, security, and compliance needs.
- Delegated Administration: Application teams manage daily operations under central governance.
- Resource Isolation: Provides secure, independent environments for workloads.
Comparison of Platform vs. Application Landing Zones
| Aspect | Platform Landing Zone | Application Landing Zone |
| Ownership | Managed by central IT teams | Managed by application teams |
| Purpose | Hosts shared services and core infrastructure | Hosts specific workloads and applications |
| Governance | Centralized, enforcing uniform policies | Governed through pre-defined policies with some autonomy |
| Operational Efficiency | Reduces duplication via consolidation of services | Optimized configurations for specific needs |
| Security & Compliance | Centralized controls and monitoring | Custom security configurations as per application |
Design Patterns for LZ
Two common landing zone design patterns, Hub and Spoke design and Virtual WAN design address different scalability, connectivity, and management requirements.
Hub and Spoke Design
A central hub (hosting shared services) connects multiple spokes (individual workloads or applications).
- Centralized Connectivity: Firewalls, VPN gateways, or ExpressRoute connections are managed centrally.
- Regional Flexibility: Suitable for single- or multi-region deployments where transitive connectivity is limited.
- Granular Routing: Allows for centralized network virtual appliances (NVAs) and controlled routing, enabling detailed traffic management.
- Scalability Considerations: Best for limited VPN connections (<100 per gateway) and centralized monitoring.
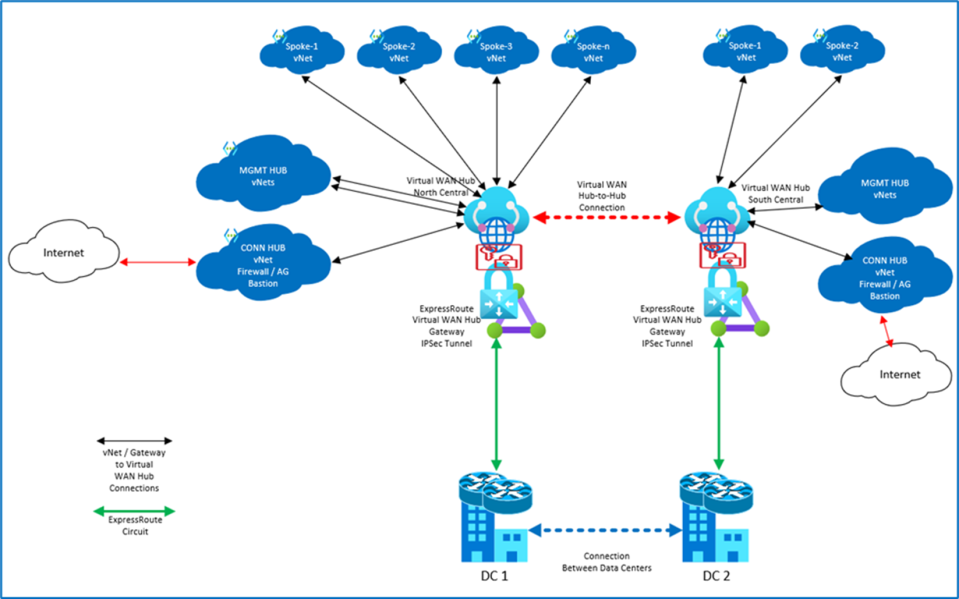
Virtual WAN Design
Virtual WAN is a Microsoft-managed solution that provides global, dynamic transit connectivity across Azure regions and on-premises locations.
- Global Connectivity: Supports any-to-any connectivity (virtual network to branch, branch to branch, etc.) across regions without manual transitive routing.
- Simplicity: Eliminates the need to manually configure complex network topologies as connectivity is managed by Microsoft.
- Enhanced Scalability: Designed for large-scale, global deployments where multiple regions and on-premises connectivity are essential.
- Centralized Resource Management: Typically deploys all resources into a single resource group within a connectivity subscription, simplifying management.

 English | EN
English | EN