Which is not the same as the ISMS*
Recently, I presented ‘information security as a process’ to a group of future Enterprise Architects. In today’s world, where digital transformation is crucial for daily business operations, information security is essential for protecting one of our most valuable assets: information. But how can we seamlessly integrate security with our existing business processes? The answer lies in the information security process: a new approach that helps organizations make choices that logically align with their business operations.
The Information Security Process: A New Approach
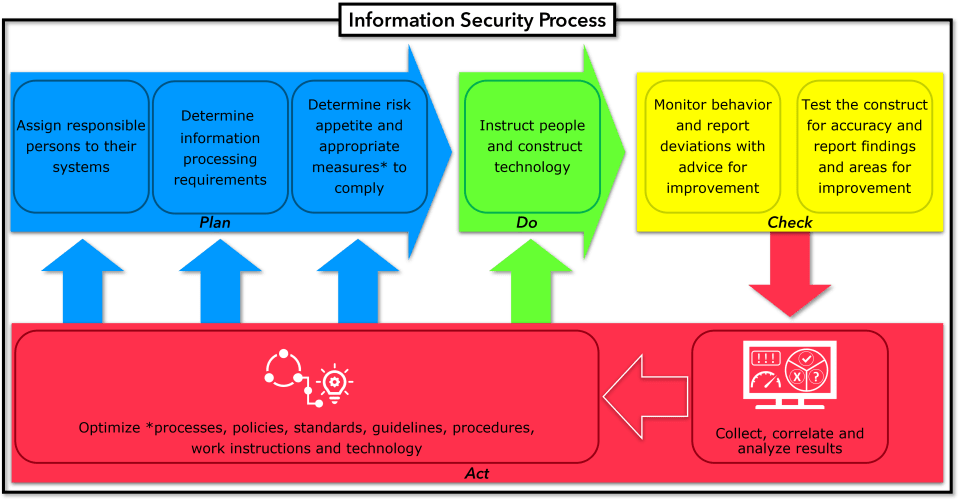
Let’s lift the veil and take a closer look at the steps of this process, starting with step one: assigning responsible persons to their systems.
1. Assignment of Responsible Persons
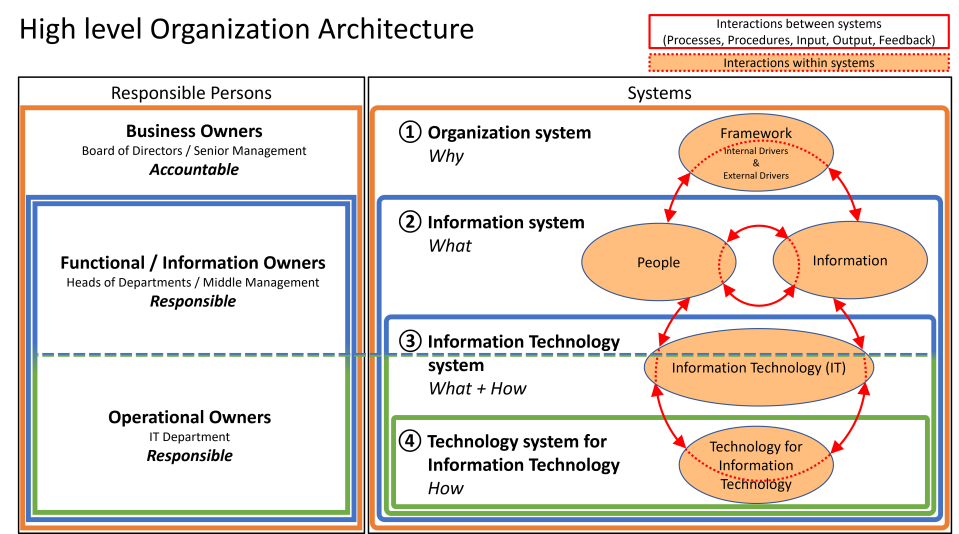
In the presentation to the Enterprise Architects, the focus was mainly on this step. Without this step, managing information security is like navigating without a compass. Enterprise architects establish how systems are structured and interrelated. As a consequence, they also determine responsibility within those systems. With this first step, we assign responsible persons to their systems and thus identify our information owners. The more detailed the elaboration, the better the control.
Think of information owners as department heads, appointed by business owners to manage their accountability on their behalf. This includes those responsible for the digital transformation of the organization. These responsible persons are all already part of your organization, so please do not create new (security) silos. Effectively use your existing workforce to jointly steer on the secure digital transformation of your organization.
By recognizing the existing expertise within our departments, we take the crucial first step towards secure digital transformation, ensuring that information owners are not only appointed but also fully equipped to manage their responsibilities and steer the organization away from unnecessary security silos.
The following figure illustrates the responsible persons within organizations and the systems that correlate to their responisbility:
2. Processing Requirements and Preferences
The designated information owners determine their processing requirements and preferences regarding confidentiality, integrity, and availability. This is where the magic begins. We listen to our information owners and apply security measures in line with the needs of the business owners.
3. Determining Mitigating Measures
Risk appetite plays an important role. Information owners determine the appropriate measures for their information (system) and indicate how much risk they are willing (or dare) to take. Remember: entrepreneurship equals taking risks, and 100% security does not exist.
4. Work Instructions and Technical Construct
The outcome of the first three steps serves as input for those who process information and for those who set up the technology to support those who process the information. We translate the outcomes into appropriate tools with instructions explaining how to use them.
5. Monitoring and Behavioral Analysis
The organization keeps an eye on things. We observe the behavior of our information processors and the technology that supports them. Deviations from the established norm? We catch and take them seriously. This way, we detect unwanted behavior in our digital house and can nip it in the bud.
6. Testing and Reporting
We want to ensure that our technical environment functions well. So we test it, just like the periodic vehicle inspection of a car. What we find, we report. No secrets, no hidden defects.
7. Analysis and Improvement
Here comes the interesting part. We collect all findings and then analyze & correlate them. Are there patterns? Are there weak spots? Then we get to work. Implement improvements, tackle unwanted practices, and minimize risks. It is an ongoing process, like an endless dance where we keep getting better at our security steps.
8. Continuous process
This is not a one-time action. The Information Security Process is continuous and repetitive. From assignment to improvement, and then back to the beginning. A single loop to steer, and double loops to optimize. This way, we remain agile, alert, and prepared for the digital challenges of tomorrow. The following illustration shows the entire process:
Conclusion
So, dear reader, let’s embrace the information security process as our new companion. Not as a replacement for already established information security structures and measures, but as an addition, for better grip and control over business operations. It is the key to a secure digital future. Confidentiality, integrity, and availability: weave them into existing business processes to enhance your digital threat resilience.
Let’s go for it: the next step in information security, where information (and its processing) is the central focal point! Dance along in the security waltz that fits the context of your organization and digitize with confidence and accepted risk!
*The Information Security Process is not the same as the Information Security Management System (ISMS). The ISMS manages the outcomes of the information security process.

 English | EN
English | EN 