What is AWS Lambda?
- AWS Lambda is a serverless computing service offered by AWS. Developers can use Lambda to execute their code in the cloud. AWS Lambda uses Lambda functions to enable the use of the most popular coding languages.
- Lambda supports multiple runtimes like DOTNet, Python, NodeJS, Ruby etc.
- Lambda is a regional service.
What is AWS Lambda@Edge?
- AWS Lambda@Edge is an extension of AWS Lambda that grants greater flexibility and lower latency to distributed Lambda functions. You can run Lambda@Edge functions with Node.js and Python.
- The benefit of Lambda@Edge is that it uses the Amazon CloudFront content delivery network (CDN) to enable you to deliver function results globally. This is in contrast to Lambda, which requires you to provision instances in each location you want to operate from.
- Lambda@Edge is a global service.
Lambda@Edge Use cases
Lambda@edge has very specific use cases some of them are as below:
- User authorization and authentication: you can authorize and authenticate users by filtering out unauthorized requests before they reach your infrastructure. For instance, you can trigger a Lambda function to authorize each user request by calling authentication services like Amazon Cognito.
- Website security and privacy: you can add HTTP security headers on all responses without modifying your application code. This helps improve privacy and security while delivering content at low latencies using CloudFront.
- Dynamic edge applications: you can combine Lambda@Edge with other AWS services when building applications at the network edge.
User and Origin Authentication
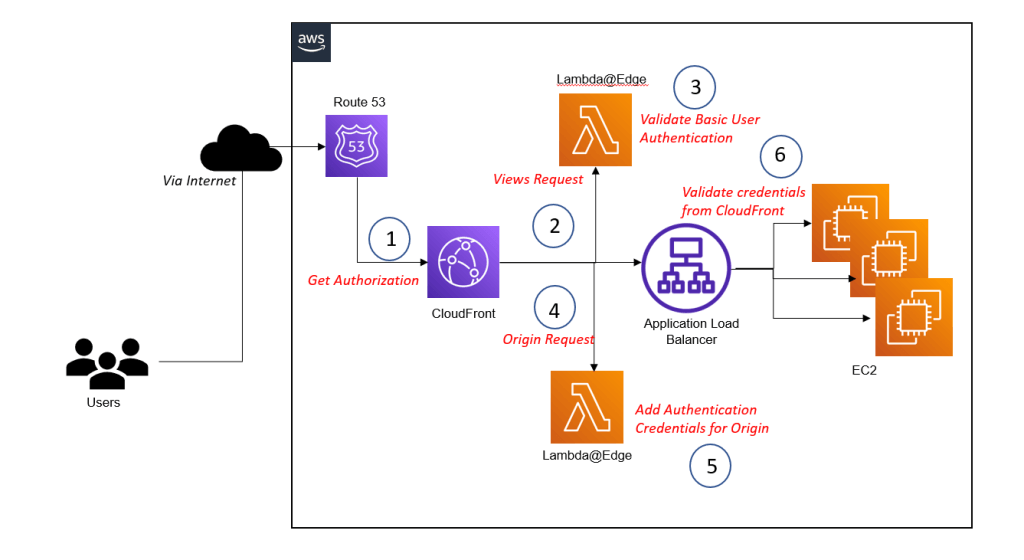
Executing code with Lambda@Edge enables to implement custom authentication. There are two major scenarios for doing so:
- Authenticate the user that tries to access media assets. For example, to restrict access to paid content.
- Add credentials when sending requests to the origin – for example, an ALB – to ensure that your web application only answers CloudFront requests. That’s important because CloudFront origins must be accessible from the Internet. Without authenticating your CloudFront distribution, it is possible to bypass the CDN. This could be used by a random hacker to send DDOS attack.
- The functionality is like the previous use cases. Configuring a Lambda@Edge function to process viewer requests allows you to authenticate a user, for example, by using basic authentication or JWT. On top of that, hooking a Lambda@Edge function into the origin request allows you to add credentials to authenticate at the origin.
Limitations using Lambda@Edge
Below are some of the limitations when using Lambda@Edge.
- Lambda@Edge does not support environment variables.
- Lambda@Edge does not support layers.
- Lambda@Edge does not support dead letter queues.
- A Lambda@Edge function for processing viewer requests comes with additional restrictions.
Maximum Memory: 128 MB
Function Timeout: 5 seconds
Response Size: 40 KB
Ref and Official for restricted use of Lambda@Edge: https://docs.aws.amazon.com/AmazonCloudFront/latest/DeveloperGuide/edge-functions-restrictions.html#lambda-requirements-lambda-function-configuration

 English | EN
English | EN 