NO PLACE TO HIDE: EXPOSING CHINAU0026#X27;S CYBER ESPIONAGE
May 19, 2014

Today, the US department of Justice announced charges against China for cyberspying on American major companies. In October 2011, US representative Mike Rogers, head of the House Intelligence Committee, had already made an appeal to Europe and Asia to confront the Chinese with their economic espionage by saying:
“China’s economic espionage has reached an intolerable level and I believe that the United States and our allies in Europe and Asia have an obligation to confront Bejing and demand that they put a stop to this piracy”.more–>

Last year, security company Mandiant published their report on a special Chinese Cyber Crime unit which they called APT1 (Advanced Persistent Threat). Twenty of these organizations were spotted by Mandiant. Their analysis has led to their conclusion that “APT1 is likely government-sponsored” and “It’s believed to be the 2nd bureau of the People’s Liberation Army – commonly known as its Military Unit Cover Designator (MUCD) unit 61398.
Reading the report it becomes clear that the ties between hacker organizations and the Chinese government are very close. After a cyber attack on the Washington Post in February 2013, the Newspaper published an article suggesting that the Chinese were behind the attack (“Chinese hackers suspected in attack on The Post’s computers“) The response of the Chinese Defense Ministry was that it is unprofessional and groundless to accuse the Chinese military of launching cyber attacks without any conclusive evidence.”
“Proof” of collaboration between nation states and these kind of organizations are seldom published, but the Mandiant report looks quite convincing. If your interested in how APT1 worked see this video or read the report yourself.
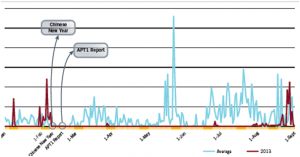
Mandiant expected reprisals from China, as well as an onslaught of criticism. That criticism would be related to the fact that unit 61398 would change their techniques after publishing about it, making it harder to continue to track them. After publishing the activities, APT1 paused for a long time. The blue line shows the activities of the year before, red line shows what happened just before and after the publication.
What are they after?
Mandiant is warning us of the risks of the Chinese government stealing intellectual property “and beyond”: executive emails, negotiation plans, meeting minutes, HR records. In 2014 they released an update in their trend report, out of which we quote:
“Across numerous industries, we’ve increasingly observed the Chinese government conduct expansive intrusion campaigns to obtain information to support state-owned enterprises. This translates into data theft that goes far beyond the core intellectual property of a company, to include information about how these businesses work and how executives and key figures make decisions”
But what makes the headlines is stealing information about weapon systems, while companies in manufacturing, energy, media and entertainment and NGO’s are being spied upon for different reasons.
No place to hide
Ironically, this month the Guardian published on how the NSA tampers with US-made internet routers. The NSA has been covertly implanting interception tools in US servers heading oversees – even though the US government has warned against using Chinese technology for the same reasons. According to the Guardian “It is quite possible that Chinese firms are implanting surveillance mechanisms in their network devices. But the US is certainly doing the same” The source behind the Guardian article is Pulitzer price winner Glenn Greenwald, who just published his book on the Snowden affair “No place to hide” (an interesting title, considering that our recent book on Big Data is called “No More Secrets”).
So indeed, after reading the Mandiant reports and the articles in the Guardian and Washington Post, the question is: is there a place to hide.? I don’t think so. This is “The New Normal”. I can’t wait until the Chinese Snowden makes himself heard.

 English | EN
English | EN